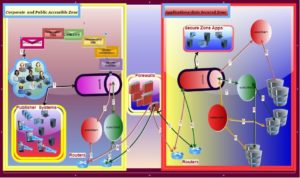
In current article, we would discuss about an event driven messaging Architecture through which a Non Secure Zone communicates through Secure Zone,Application within and out of Secure Zone,Publishers,Subscribers,routers,Firewalls,Databases,Queues
Lets take the architecture mentioned above(picture) and describe the salient points
-
Public Zone:
On left side have designed public zone for user and applications to publish events/messages in public zone.
-
Private Zone:
On right side have designed private zone which is accessible by private applications through secure private communications.
-
Public-Private Zone:
There are situations when customer facing public application needs to access private zone to store sensitive customer profile data in private zone. This is achieved through making certain public zone appliances to communicate with private zone appliances.
Architecture Elaboration:
In above picture the whole End-to-End communication has been discussed through 1-8 sequence flows.
-
Process 1:
In above architecture process->1 is process of publishing message format by customer facing/Agent facing/back office/Admin etc.. applications publisher or background batch jobs publishing or automated applications etc.. Please note that some of the 1’s are done in public queues and Some on private queues
-
Process 2:
In above architecture process->2 is process of consumption of messages/events by public zone consumers/listeners/subscribers which subscribe to the queues , process messages,responds back or passes it onto secure zone for further processing.
-
Process 3:
In above architecture process->3 communication process between consumers and routers, there are few messages public zone consumers likes to sends it to private zone consumers. Router roles play a good role to encapsulate and route the sensitive packets to private zone.
-
Process 4:
In above architecture process-4 is communication between router and firewall. Firewall plays a great role in encrypting or adding secure header bits before routing to the proper secure zone.
-
Process 5:
In above architecture process-5 is process of firewall passing the packets to secure zone internal routers so that the packets can reach to proper secure destination
-
Process 6:
In above architecture process-6 is processed router transmitting/publishing the secure, encapsulated, encrypted message packets to secure zone queue from where the consumers of the secure zone can poll the messages and process it through.
-
Process 7:
In above architecture process-7 is process of consumption of secure messages ,decryption of message packets through synchronous or asynchronous mechanism and process it further.
-
Process 8:
In above architecture process-8 is process of subscriber/consumer consuming message and inserting/updating/retrieving various RDBMS that has been implemented in architecture
Hence Overall at the end-to-end level, the whole process can be summarized as below
Through public zone applications customer profile data, sensitive information like email addresses/credit card/order information/email address/phone number etc would be published to public queues. in addition to the same, batch process, automated processes, mobile /tablet communication data would also be published in queue public subscriber processes would subscribe the various types of messages and would process and pass on the sensitive information to private queues via router and firewall. Private consumers /subscriber would further consume the messages, store into secure databases for further usage. In addition to the same, some private applications which are there in a secure zone would also publish messages to the same queues and get combined to traffic. this is how public-private communication would get established.
How do we test this Architecture
This Can be tested through tested through End to End or Component Level in atomic or combined mode. END-to-End: All the Performance test types can be performed by driving the traffic through End-to-End Test in a few ways.
 Application Scripting:Thin client(Costly Path): As per this approach. A performance testing team has to engage there team members to script the thin UI client through daily used business case scenarios using any performance scripting tool record and replay functionality. To me, If I have to test the efficiency of the application, I would take this path, but for testing message queue this could be a costly path. A reason could be that each application needs to be scripted and any small or big change can make a re-scripting effort spanning 5+ days. so scripting, coordination effort is more.
Application Scripting:Thin client(Costly Path): As per this approach. A performance testing team has to engage there team members to script the thin UI client through daily used business case scenarios using any performance scripting tool record and replay functionality. To me, If I have to test the efficiency of the application, I would take this path, but for testing message queue this could be a costly path. A reason could be that each application needs to be scripted and any small or big change can make a re-scripting effort spanning 5+ days. so scripting, coordination effort is more.
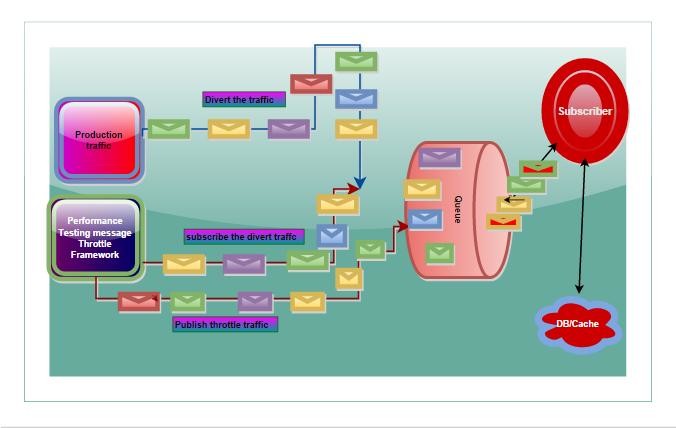
Queue Tapping Framework(Cost Effective Path): At End to End level this path could be very useful. In one of my article, I have mentioned the approach for throttling based load. a similar approach can be taken here. Alternatively, The application traffic can be simulated at the message tier level through various formats. formats are generally schema-based and thus changes in the schema can enable performance scripting person to move ahead with a few changes in the test-driven code. Below technique is called “Divert and Steal then Fill At Will”( called by me though)
Component Level: Here in the current Architecture there are two messaging components. One is in public zone and another one is in the Private zone. both the zone is a connection through router and firewall. So latency could be at the application level or could be at the network level too. So to determine that delta value of the latency we must do below
Perform performance test on Subscriber capacity at Public Zone in atomic mode. calculate the message processing power
Perform performance test capacity at Private Zone in atomic mode. calculate the message processing power
Perform performance test capacity by driving the test through Public Zone and monitor the Public-Private zone message process capacity. Based on stats of 1 and 2, delta value will help in generating near to accurate message processing capacity report at the end to end level too

